Sanitizers
Sanitizer 简介
Sanitizer 是一个动态 Bug 检测的工具,它可以检测的 Bug 有以下几类:
- 内存越界
- 内存未初始化
- 内存泄漏
- 死锁
- 未定义行为 (UB)
内存 Bug
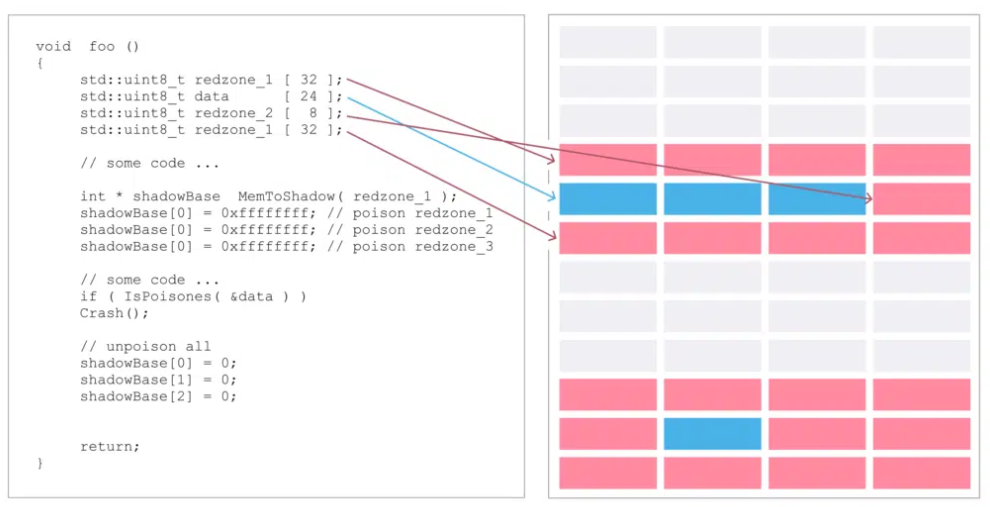
Sanitizer 检测内存越界,未初始化,泄漏的原理是让编译器在程序真正使用的内存周围加上额外的内存 (Red Zone), 并在这些 Red Zone 里填上不同的值。
要完成这些需要让程序链接一个叫 libasan.so 的运行时动态库,以及在编译和链接时指定 -fsanitize=address。
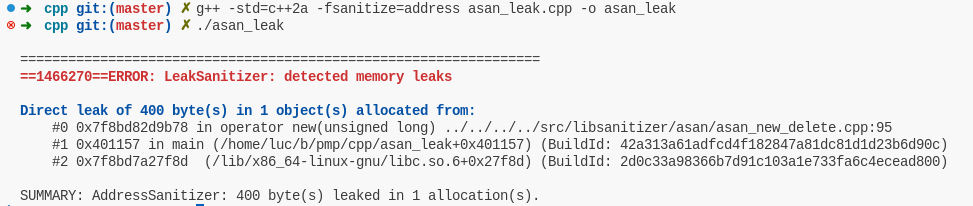
- AddressSanitizer (ASan
-fsanitizer=address):- use-after-free
- double-free
- buffer (heap, stack, and global buffer) overflows
- memory leak
1 | struct Foo { |
- MemorySanitizer (MSan
-fsanitizer=memory -fsanitizer-memory-track-origins):- uninitialized memory reads
死锁
- ThreadSanitizer: data races, deadlocks
未定义行为
- UndefinedBehaviorSanitizer (UBSan
-fsanitizer=undefined)- signed integer overflow
- use-of-null-pointer
- division by zero